Security Awareness Training
Solve the #1 root cause of data breaches
Conform to Audit and Regulatory Compliance
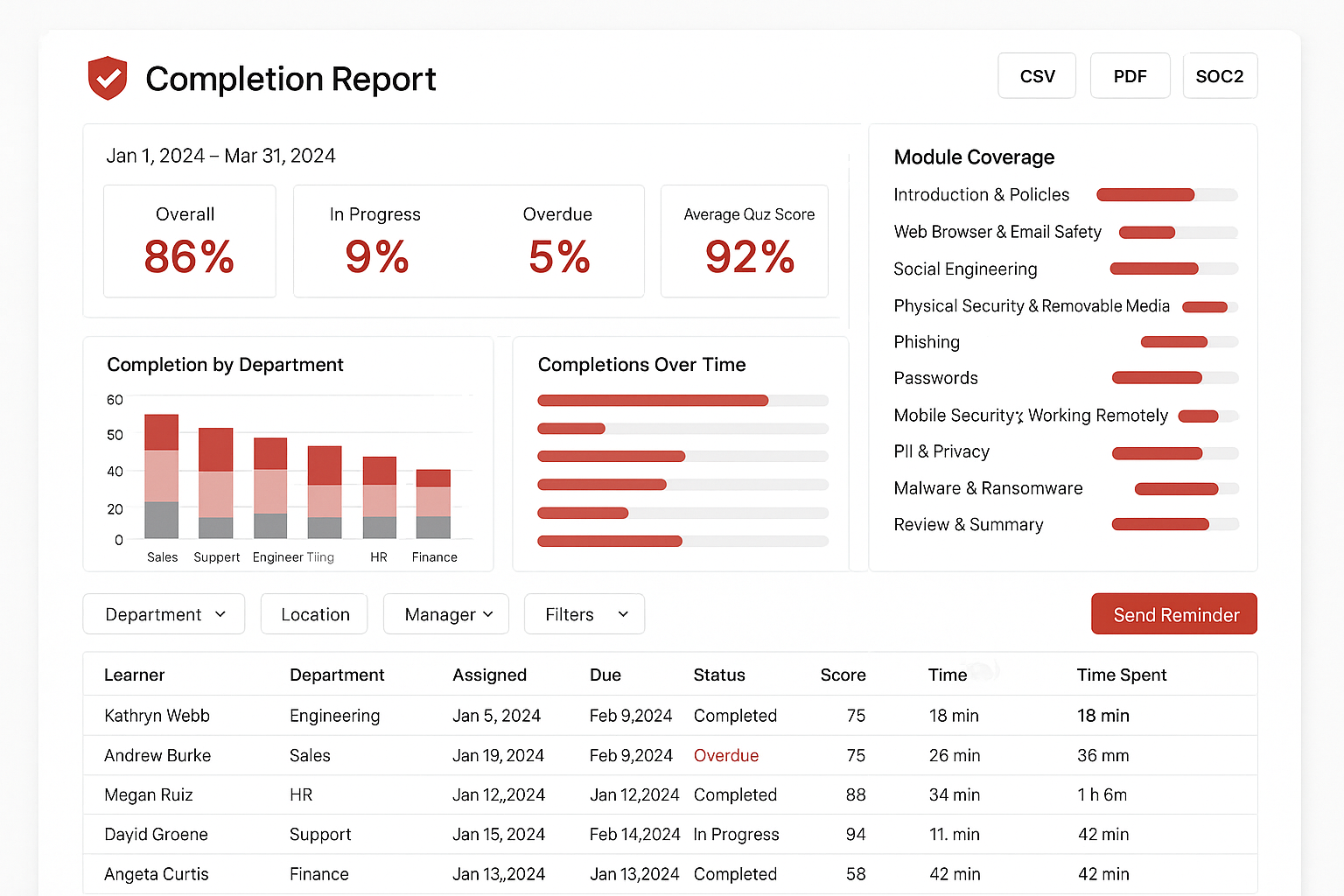
Prove control effectiveness with documented training, testing, and risk treatment. Generate auditor-ready evidence that maps to SOC 2, ISO 27001, HIPAA, PCI-DSS, and more.
- Policy attestations and completion tracking for every employee.
- Centralized artifacts: reports, risk register, and remediation evidence.
Address Security Framework Requirements
Align people, process, and technology to NIST CSF/800-53/800-30 and CIS Controls. Close gaps with prioritized actions and measurable outcomes.
- Mapped controls for training, testing scope, and risk treatment plans.
- Board-ready dashboards and heatmaps to track progress.
Cyber Informed - Security Awareness Training
Turn your team into your strongest defense with concise, engaging lessons and automated reinforcement
What your team will master
Ten focused modules covering everyday, real-world risks.
Introduction & Policies
Expectations, acceptable use, incident reporting, and why awareness matters.
Web Browser & Email Safety
Safe browsing, attachments, links, and spotting spoofed senders.
Social Engineering
Pretexting, baiting, tailgating, and how to verify before you trust.
Physical Security & Removable Media
Clean desk, badge usage, visitor control, and USB/portable media risks.
Phishing
Recognize and report phishing across email, SMS, chat, and social platforms.
Passwords
Strong passphrases, managers, MFA, and avoiding reuse across services.
Mobile Security & Working Remotely
Device updates, secure Wi-Fi/VPN, screen locks, and protecting on the go.
PII & Privacy
Handling personal data, minimal collection, consent, and data sharing basics.
Malware & Ransomware
Common infection paths, safe installs, backups, and what to do if hit.
Review & Summary
Final recap, policy acknowledgement, and certificate of completion.
Launch in three steps
Deploy to your whole organization or targeted groups with SSO and automated reminders.
Set cadence, due dates, and reminders.
Auto-nudges keep training on track—no manual chasing required.
See progress by group, manager, and timeframe.
Why teams choose Cyber Informed
Fast rollout, clear content, and the proof you need for customers and audits.
-
Lightning-fast rollout: SSO or CSV import. Start training in minutes.
-
Plain-English lessons: Non-technical, bite-size modules that drive real behavior change.
-
Hands-off reminders: Auto-nudges and manager views keep progress on track without babysitting.
-
Audit-ready proof: Completion records, quiz scores, and policy sign-offs for customers and regulators.